With Azure SQL Database Threat Detection, Microsoft aims to provide a new layer of security to your Azure SQL database by detecting abnormal database activities which may indicate a common threat like SQL injection being the most common database attack.
This feature will help customers detect and respond to potential threats as they occur, receiving instant actionable notifications when set up. A customer can immediately explore the potential threat by using SQL database auditing to further determine if the event is the result of an attempt to access, breach or exploit data in the database.
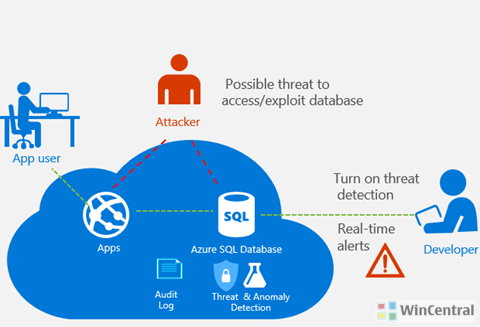
After nearly a year in preview (since 2015, when it was first announced), receiving the customer feedback to near about 90% (regarding the usefulness of SQL threat alerts), Microsoft is proud to announce that Azure SQL Database Threat Detection will be generally available in April 2017. At general availability, SQL Database Threat Detection will cost of $15 / server / month. However, you can try out the service free, for 60 days.
The benefits of Azure SQL Database Threat Detection include:
- Simple configuration of SQL threat detection policy via Azure portal.
- Clear email alerts upon detection of suspicious databases queries indicating potential SQL injection events.
- Ability to explore the audit log around the time of the event using the Azure portal or pre-configured excel template.
- No need to modify database procedures or application code.
How to set up Threat Detection
You need to start with the latest service version of SQL Database (V12) and configure Threat Detection for your database with a few simple steps in the Azure management portal.
- Launch and sign in to the Azure portal.
- Navigate to the configuration blade of the SQL Database you want to monitor. In the Settings blade, select Auditing & Threat Detection.
- Turn ON auditing, which will display the Threat detection settings.
- Turn ON Threat detection and configure the list of emails that will receive security alerts upon detection of anomalous database activities.
- Click Save to save the new or updated auditing and threat detection policy.
Note: Enabling Threat Detection requires that Auditing be turned on and at least one configured email address to receive notifications.
Threat Detection Demo
Check out the Threat Detection demo, which demonstrates a walkthrough of the setup, detection and investigation experience of a SQL injection attack.