Microsoft today made two major Defender ATP announcements. While Microsoft Defender ATP for Linux is now generally available, the Defender ATP for Android public preview has just been announced.
First, coming to the Microsoft Defender ATP for Linux, it supports recent versions of the six most common Linux Server distributions. It can be deployed and configured using Puppet, Ansible, or using the existing Linux configuration management tool.
- RHEL 7.2+
- CentOS Linux 7.2+
- Ubuntu 16 LTS, or higher LTS
- SLES 12+
- Debian 9+
- Oracle Linux 7.2
Read more about Microsoft Defender ATP for Linux here.
Microsoft also announced the public preview of Microsoft Defender ATP for Android. This is how you can get started with the ATP for Android.
Getting started with Microsoft Defender ATP for Android
Those customers that have preview features turned on can start trying out Microsoft Defender ATP for Android today. If you haven’t yet opted in, we encourage you to turn on preview features in the Microsoft Defender Security Center today.
Join us as we advance in our journey across platforms. For more information, including detailed system requirements, prerequisites, deployment and configuration steps, and a list of improvements and new features, check out the documentation.
Here are the official details of the key features of Microsoft Defender ATP for Android.
Key Capabilities
The public preview of Microsoft Defender ATP for Android will offer protection against phishing and unsafe network connections from apps, websites, and malicious apps. In addition, the ability to restrict access to corporate data from devices that are deemed “risky” will enable enterprises to secure users and data on their Android devices. All events and alerts will be available through a single pane of glass in the Microsoft Defender Security Center, giving security teams a centralized view of threats on Android devices along with other platforms. These capabilities empower enterprises to enable strong security while ensuring their employees remain productive working on their Android devices. Let’s dive into each of these capabilities in more detail.
Web protection
Phishing is one of the biggest threat vectors on mobile, with the majority of attacks happening outside of email such as via phishing sites, messaging apps, games, and other applications. Other potential threats come from apps which may make connections to unsafe domains, unknowingly to the user and security teams. Web protection capabilities in Microsoft Defender ATP for Android help to address these challenges with:
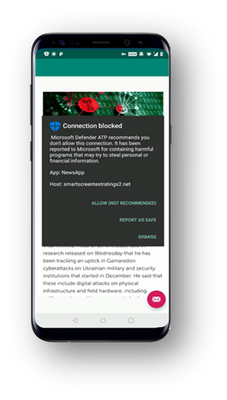
- Anti-phishing: Access to unsafe websites from SMS/text, WhatsApp, email, browsers, and other apps is instantly blocked. To do this, we leverage the Microsoft Defender SmartScreen service to help determine whether a URL is potentially malicious. This works in conjunction with Android to enable the app to inspect the URL to provide anti-phishing protection. If access to a malicious site is blocked, the device user will get a notification about this with the options to allow the connection, report it safe, or dismiss the notification. Security teams are notified about attempts to access malicious sites via an alert in the Microsoft Defender Security Center.
- Blocking unsafe connections: The same Microsoft Defender SmartScreen technology is used to also block unsafe network connections that apps automatically might make on the user’s behalf without them knowing. Just as in the phishing example, the user is immediately informed that this activity is blocked and is given the same choices to allow it, report it as unsafe, or dismiss the notification as the product screenshot shows. Alerts for this scenario also show up in the Microsoft Defender Security Center. When these connections are attempted on a user’s device, security teams are notified of this via an alert in the Microsoft Defender Security Center.
- Custom indicators: Security teams can create custom indicators, giving them more fine-grained control over allowing and blocking URLs and domains users connect to from their Android devices. This can be done in the Microsoft Defender Security Center and is an extension of our custom indicators capability already available for Windows.
Malware scanning
Enterprises deploying Android can leverage built-in protections in the Android platform to limit installation of apps to trusted sources as well as tools like Google Play Protect to significantly reduce the threat surface of potentially harmful apps being installed on devices. Microsoft Defender ATP fortifies this by introducing additional visibility and controls to deliver further assurances on keeping devices free of threats to device security.
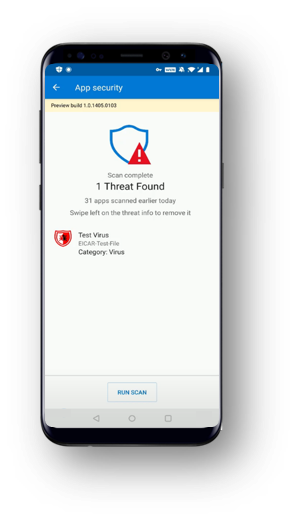
Microsoft Defender ATP for Android uses cloud protection powered by deep learning and heuristics to provide coverage for low-fidelity signals which are inconclusively handled by signatures, in addition to offering signature based malware detection. This protection extends to both malicious apps and files on the device.
Scans are instantly performed detect malware and potentially unwanted applications (PUA). If a safe app is downloaded, the end user will see a lightweight notification letting them know the app is clean.
Blocking access to sensitive data
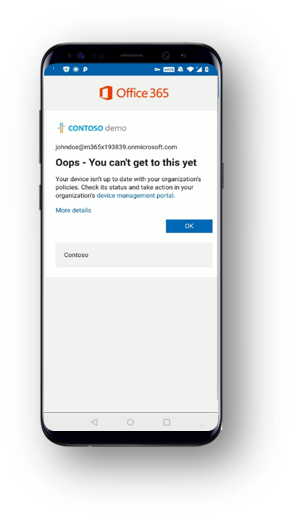
Additional layers of protection against malicious access to sensitive corporate information is offered by integrating with Microsoft Endpoint Manager, which includes both Microsoft Intune and Configuration Manager. For example, a compromised device would be blocked from accessing Outlook email. When Microsoft Defender ATP for Android finds that a device has malicious apps installed, it will classify the device as “high risk” and will flag it in the Microsoft Defender Security Center. Microsoft Intune uses the device’s risk level in conjunction with pre-defined compliance polices to activate Conditional Access rules that block access to corporate assets from the high risk device. The screenshot shows an example of how the end-user would get a notification that their device doesn’t comply with their organization’s policies, and how to remediate. Once the malicious app is uninstalled, access to corporate assets is restored automatically for the mobile device. You can learn about how to set up this integration in our documentation.
Unified SecOps experience
The Microsoft Defender Security Center acts as the single pane of glass experience for security teams to get a centralized view of threats and activities. All the alerts for phishing and malware on Android devices are surfaced here. As part of the alert, analysts see the name of the threat, its severity, the alert process tree for the incident, and other additional context including file details and associated SHA information. Android device related alerts also roll up into the incident where analysts can get a more holistic view of attacks associated with a device.
In the devices list, Android devices are also visible with their associated risk levels. In the device information page, security analysts can see the number of incidents, active alerts, and logged on users associated with the device.









![[Video] How to Install Cumulative updates CAB/MSU Files on Windows 11 & 10](https://i0.wp.com/thewincentral.com/wp-content/uploads/2019/08/Cumulative-update-MSU-file.jpg?resize=356%2C220&ssl=1)



![[Video Tutorial] How to download ISO images for any Windows version](https://i0.wp.com/thewincentral.com/wp-content/uploads/2018/01/Windows-10-Build-17074.png?resize=80%2C60&ssl=1)




